Cybersecurity Solutions and Compliance
Alien Intelligence delivers practical cybersecurity and compliance solutions for Australian businesses that need protection, resilience, and continuity without unnecessary complexity. We focus on reducing real risk, improving visibility, and ensuring your security posture can stand up to the ever evolving threat landscape. You can reduce your risk and become a tougher target!
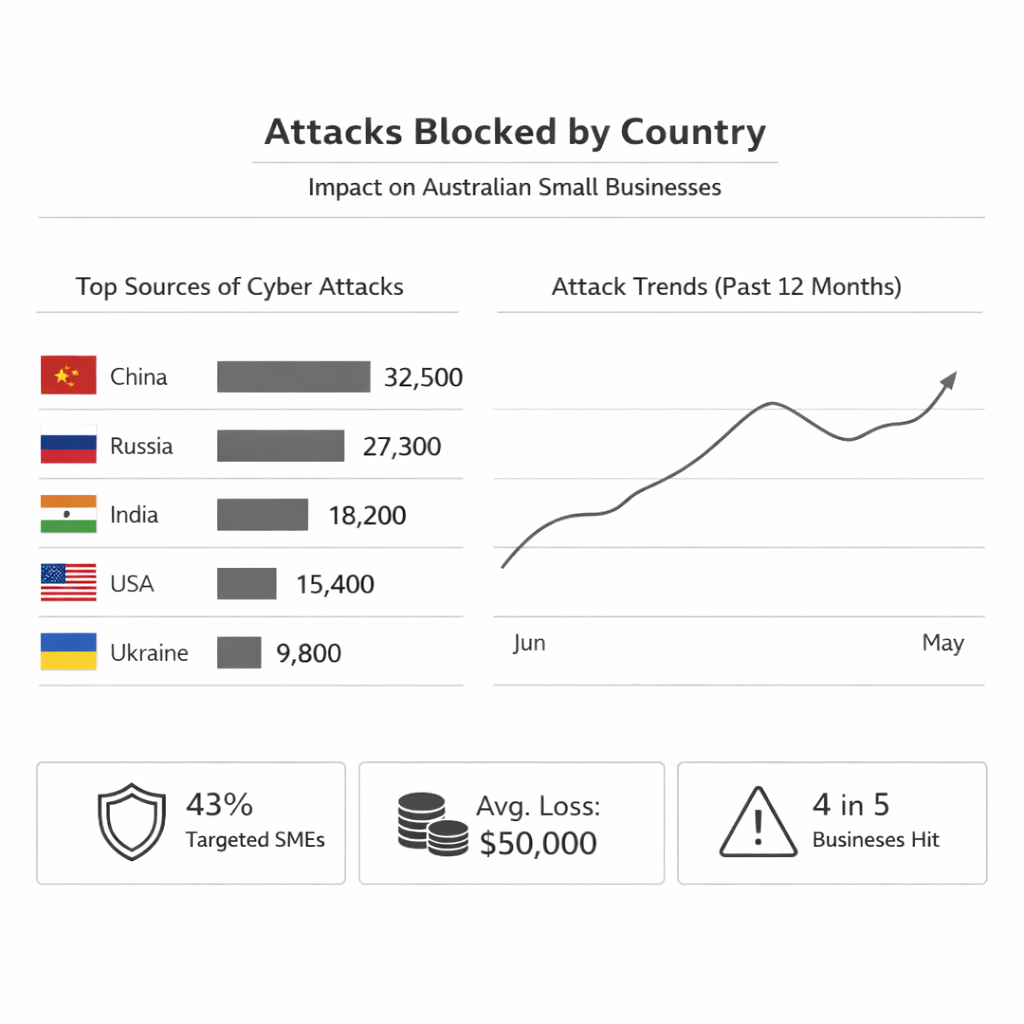
Cyber Attacks on Australian Businesses
Avg Loss to a
Small Business
Avg Loss to a
Medium Business
Aimed at Small Businesses
Not Surviving a
Major Incident
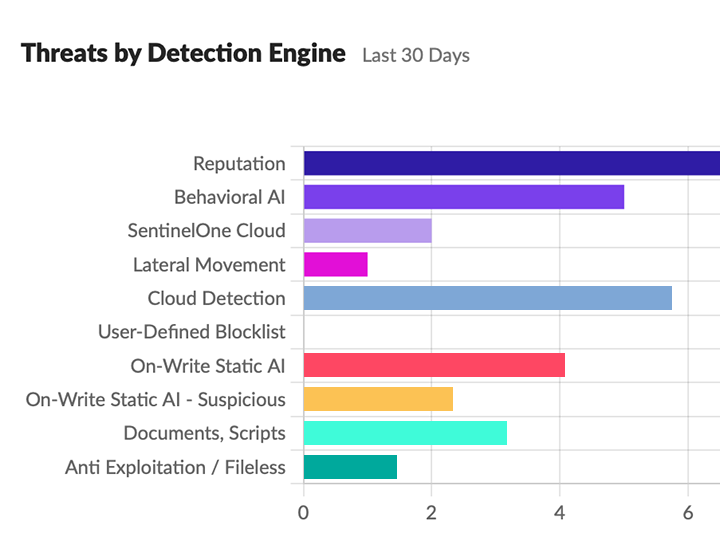
Building Security In, Not Kicking Productivity Out
Good cybersecurity should make your business look like a tough target whilst not slowing you down. We design security solutions that reduce exposure without disrupting productivity. Alongside our partners we have delivered a proven model designed to protect people, systems, and data, while maintaining compliance requirements. It allows the business to operate with confidence and scale without security debt. Security is not just a set of products you buy, it’s a set of decisions designed into the environment.
AI Powered Endpoint Protection (EDR) and Threat Monitoring
24/7 advanced endpoint protection continuously monitors behaviour to detect and stop threats before they can spread.
Managed Detection and Response (MDR)
Security events are monitored and responded to in real time, with incidents investigated, contained, and clearly reported.
AI Powered Security Information and Event Management (SIEM)
Security events from across your environment are centrally analysed to provide visibility, context, and actionable insight.
Email and Collaboration Security
Email and collaboration platforms are protected against phishing, malware, and unauthorised access without disrupting productivity.
Vulnerability and Update Management
Systems are continuously assessed and updated to reduce known weaknesses and prevent exploitable gaps.
Business Continuity, Backup, Recovery, and Ransomware Resilience
Data and systems are protected with resilient recovery strategies that ensure rapid restoration in case of incidents or attacks.
Endpoint Privilege Management (EPM) and Automated Elevation Control
Administrative privileges are restricted and granted only when needed, reducing risk while maintaining productivity.
Zero Trust Application Control
Only explicitly approved applications are allowed to run, blocking unauthorised software by default.
Secure Configuration and Hardening
Systems are configured to minimise attack surfaces by enforcing secure settings and removing unnecessary exposure.
Staff Security Awareness Training
Ongoing training helps staff identify and safely handle phishing, social engineering, and everyday security risks.
Identity and Access Security
User identities and permissions are tightly controlled to ensure access is appropriate, auditable, and secure.
Penetration Testing & Advanced Security Assessments
Targeted security testing identifies real-world weaknesses and provides clear remediation guidance.

Policies Built for People
Security only works when it’s humanised, governed and clearly communicated. We help our customers define security ownership and accountability, document policies and procedures, align controls to recognised frameworks, and demonstrage their security posture for audits, tenders, and cyber insurance requirements. This approach governs our services, the IT roadmap and your staff IT usage. Our compliance work is designed for defensible outcomes, not paperwork for its own sake.


Standardise Controls
One easy to understand set of controls for your environment, non intrusive and staff oriented.
Demonstrate Posture
Fully aligned with security standards allowing you to easily demonstrate posture for tenders, insurers, auditors or customers.
Unify IT Decisions
Security becomes the core of your IT environment, influencing decisions for IT management, cloud vs on premise solutions, procurement and remote work


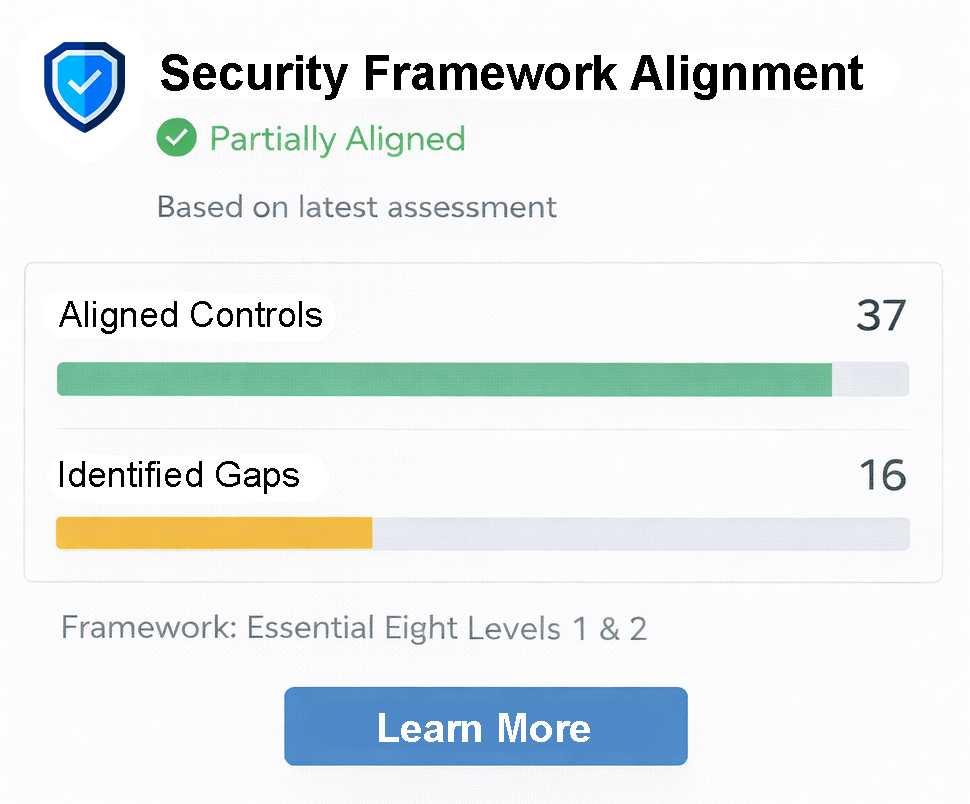
Alignment with Cybersecurity Frameworks
We align security controls to frameworks such as:
• ASD Essential Eight, ISO 27001, SMB1001 and others
• Common Australian cyber insurance requirements
• Industry-specific governance expectations
We help you understand:
• Where you are today in the cybersecurity journey.
• What maturity looks like for your organisation.
• How to improve progressively without disruption.
Current State & Maturity Assessment
We assess your existing security controls to establish a clear, evidence-based baseline.
Practical Framework Alignment
Security controls are mapped to relevant frameworks in a way that reflects how your business actually operates.
Priority-Led Improvement Planning
We identify which improvements deliver the greatest risk reduction first, avoiding unnecessary work.
Evidence & Documentation Readiness
Controls and processes are documented to support audits, tenders, and insurance requirements.
Progressive Maturity Uplift
Security maturity is improved in manageable stages without disrupting operations.
Ongoing Alignment & Review
Framework alignment is reviewed and updated as your environment, risks, and obligations evolve.
Get Your Free Cybersecurity Health Check Today!
Get a practical assessment of your current security posture and a clear path forward. Identify risks, vulnerabilities, and improvement opportunities in a single, structured review.



How We Engage on Security
We follow a structured, measurable process:
1. Security Review & Risk Assessment - Understand current controls, exposure and maturity.
2. Priority-Led Recommendations - We build a roadmap and prioritise it with you by focusing on controls that matter most.
3. Implementation & Hardening - Deploy and configure security properly.
4. Governance & Documentation - Make controls understandable and visible to the organisation.
5. Ongoing Oversight - Maintain, monitor, and improve over time.
No scare tactics. No rushed decisions. Just steady risk reduction.


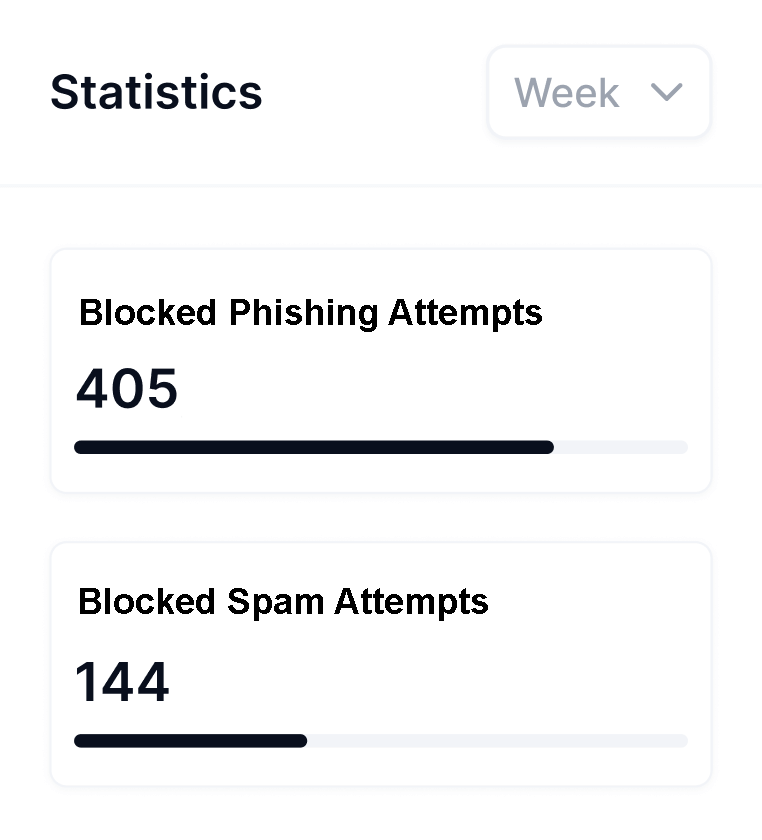

What Clients Typically Experience
While every environment is different, organisations often see:
• Clearer visibility into cyber risk
• Reduced attack surface and exposure
• Improved alignment with industry standard controls
• Increased confidence from leadership and stakeholders
• Stronger positioning for insurance, audits, and tenders
Security becomes understood and manageable, not abstract and not seen as a restriction. We see staff members contributing and participating rather than avoiding security controls.
