Why Most Cyber Incidents Start With Small Gaps, Not Major Failures
When cyber incidents make the news, they’re often described as sophisticated attacks or major breaches. In reality, most incidents don’t begin with complex techniques, they start with small, overlooked gaps in everyday systems and processes.
Why Most Cyber Incidents Start With Small Gaps, Not Major Failures
When cyber incidents make the news, they’re often described as sophisticated attacks or major breaches. In reality, most incidents don’t begin with complex techniques, they start with small, overlooked gaps in everyday systems and processes. These gaps are rarely dramatic on their own. The risk comes from how quietly they accumulate.
The Myth of the “Big Hack”
There’s a common perception that cyber incidents are caused by:
- advanced attackers
- zero-day exploits
- highly targeted campaigns
While those do exist, they are far less common than simple, preventable failures.
In most cases, incidents begin with something far more ordinary.
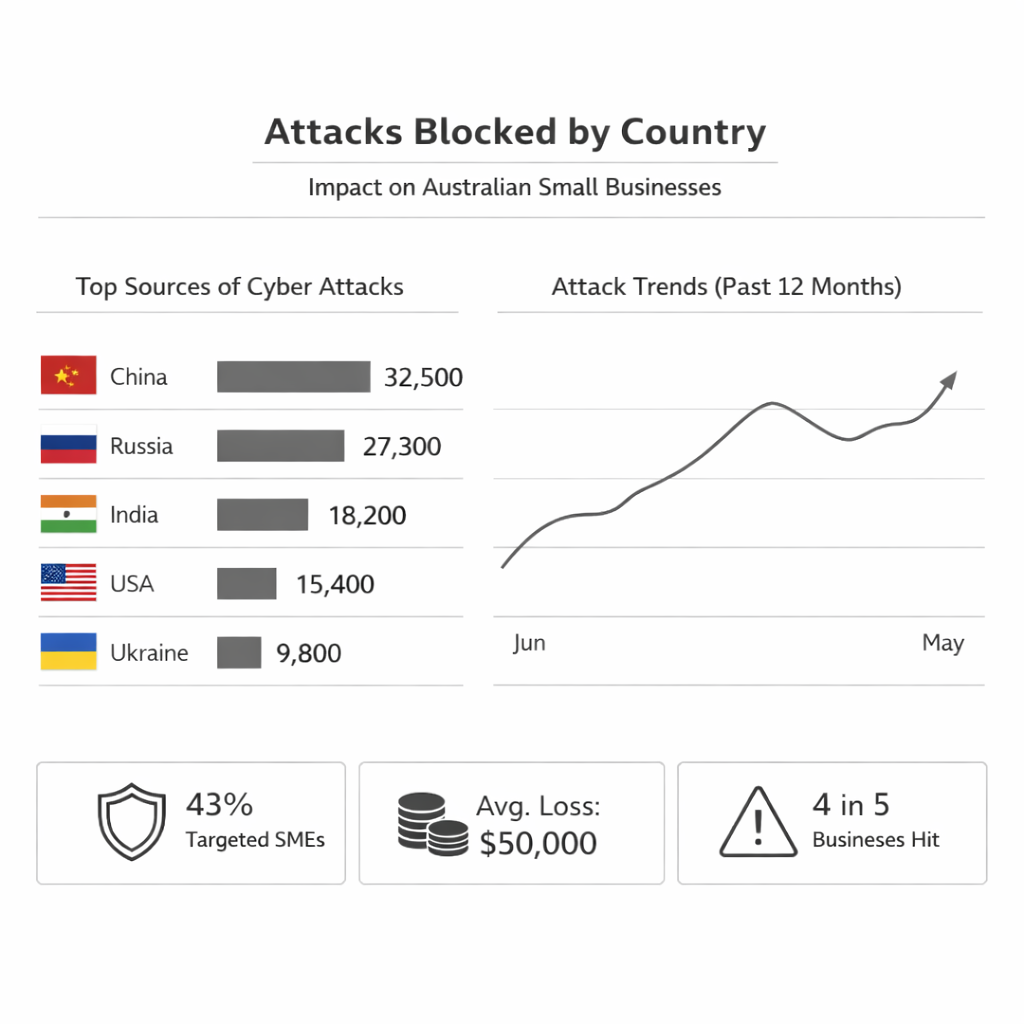
Where the Gaps Usually Appear
Small gaps tend to form in areas that feel routine or low-risk.
Common examples include:
- unused accounts that were never removed
- software updates delayed “until later”
- overly broad access permissions
- security tools that were deployed but never fully configured
- assumptions that someone else is monitoring the environment
Individually, these don’t look dangerous. Together, they create opportunity.
How Small Gaps Turn Into Real Incidents
Attackers don’t need everything to fail, they only need one opening.
A typical progression looks like this:
- a minor weakness is discovered
- access is gained quietly
- movement happens inside the environment
- activity goes unnoticed due to lack of visibility
- impact occurs much later, often unexpectedly
By the time the issue is detected, the original gap is long forgotten.
Why These Gaps Go Unnoticed
Small security gaps are easy to miss because:
- systems appear to be “working fine”
- no single person owns overall security posture
- responsibilities are spread across tools and vendors
- issues don’t surface until something breaks
Without clear ownership and regular review, gaps persist simply because nothing is forcing them to close.
Security Is About Coverage, Not Perfection
Effective cybersecurity isn’t about eliminating all risk. It’s about reducing exposure consistently over time.
This means:
- ensuring basic controls are properly implemented
- reviewing access and configuration regularly
- monitoring for unusual behaviour
- closing gaps before they’re exploited
Small, routine improvements often reduce more risk than large, one-off projects.
The Value of a Structured Approach
Organisations that experience fewer incidents tend to have one thing in common: structure.
Structure provides:
- clear ownership of security decisions
- visibility into what’s in place and what’s not
- regular review instead of reactive fixes
- confidence that controls are doing what they should
This doesn’t require enterprise-scale complexity — it requires intent and follow-through.
Final Thought
Most cyber incidents don’t start with major failures. They start with small gaps that went unnoticed for too long. By identifying and closing those gaps early, organisations dramatically reduce the likelihood of serious incidents often without significant disruption or cost.